A new era has arrived – High Velocity CEM™
Everbridge High Velocity Critical Event Management (CEM), powered by Purpose-built AI.
The increasing frequency of critical events is reshaping board priorities and challenging continuity. Everbridge allows organizations to stay ahead of physical and digital threats such as weather events, active assailants, and IT disruptions.
Know earlier about potential threats
Respond faster
Improve continuously in how you deal with threats
With Everbridge your organization is more agile, competitive and profitable
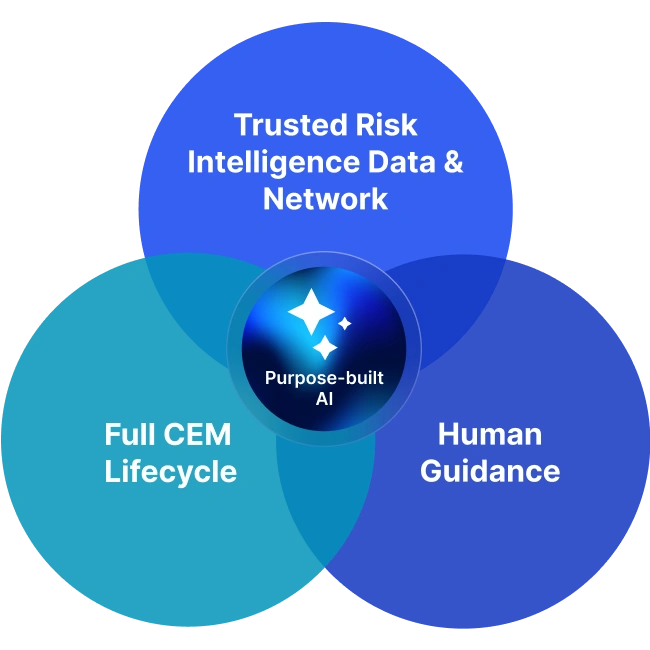
Everbridge 360™
Managing critical events is as easy as 1-2-3
Our High Velocity CEM platform, Everbridge 360, demonstrates our unwavering commitment to full lifecycle automation, and providing our customers with the most comprehensive, user-friendly solution for managing critical events.
Optimize responses, minimize communication delays, and enhance organizational resilience, all in one intuitive platform.

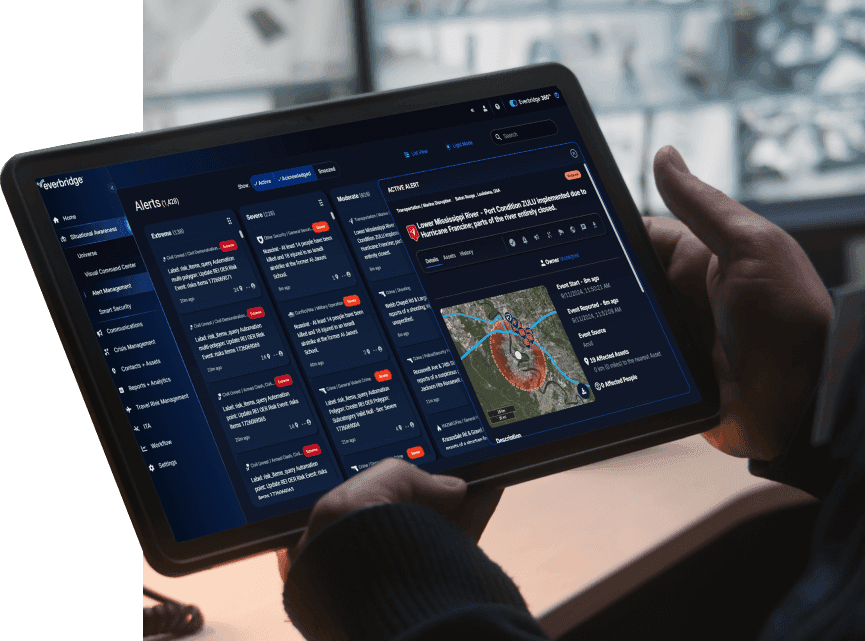
1. Know earlier
With advanced business continuity planning and leading risk intelligence, all driven by Purpose-built AI, you’ll get real-time insights to detect threats wherever they arise, helping you quickly identify risks to your people and operations.
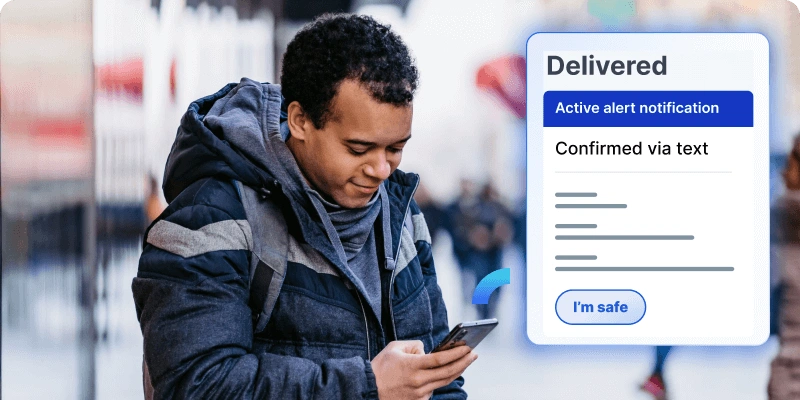
2. Respond faster
When critical events happen, speed matters. Our Alert Management feature enables seamless, “one-click” automation, from emergency communications to clear instructions, keeping your employees safe and your business protected.
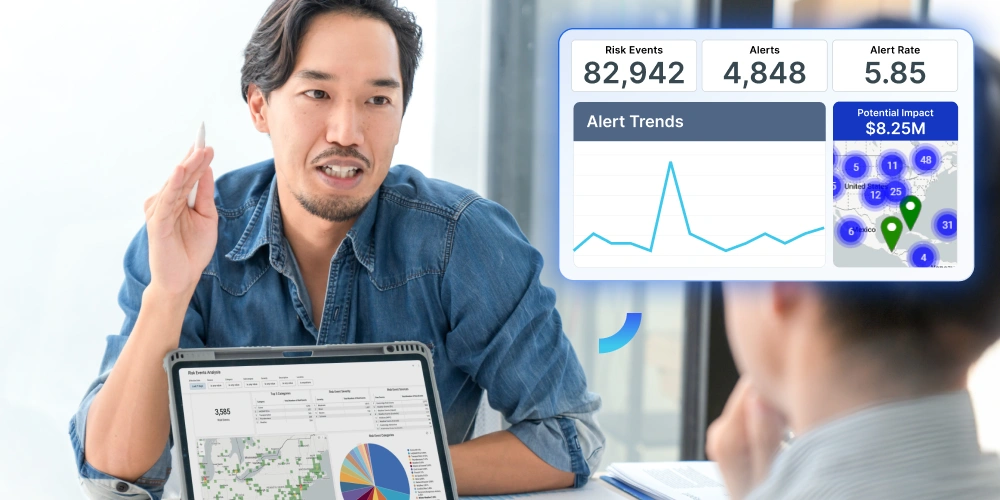
3. Improve continuously
Adapt and improve with our AI-powered differentiators: detailed after-action reports, response analytics, and interactive dashboards. Turn data into insights to strengthen your organization’s resilience for the future.
Everbridge High Velocity CEM
Protect your organization from the impact of critical events, and achieve a business resilience advantage, with Everbridge High Velocity CEM.
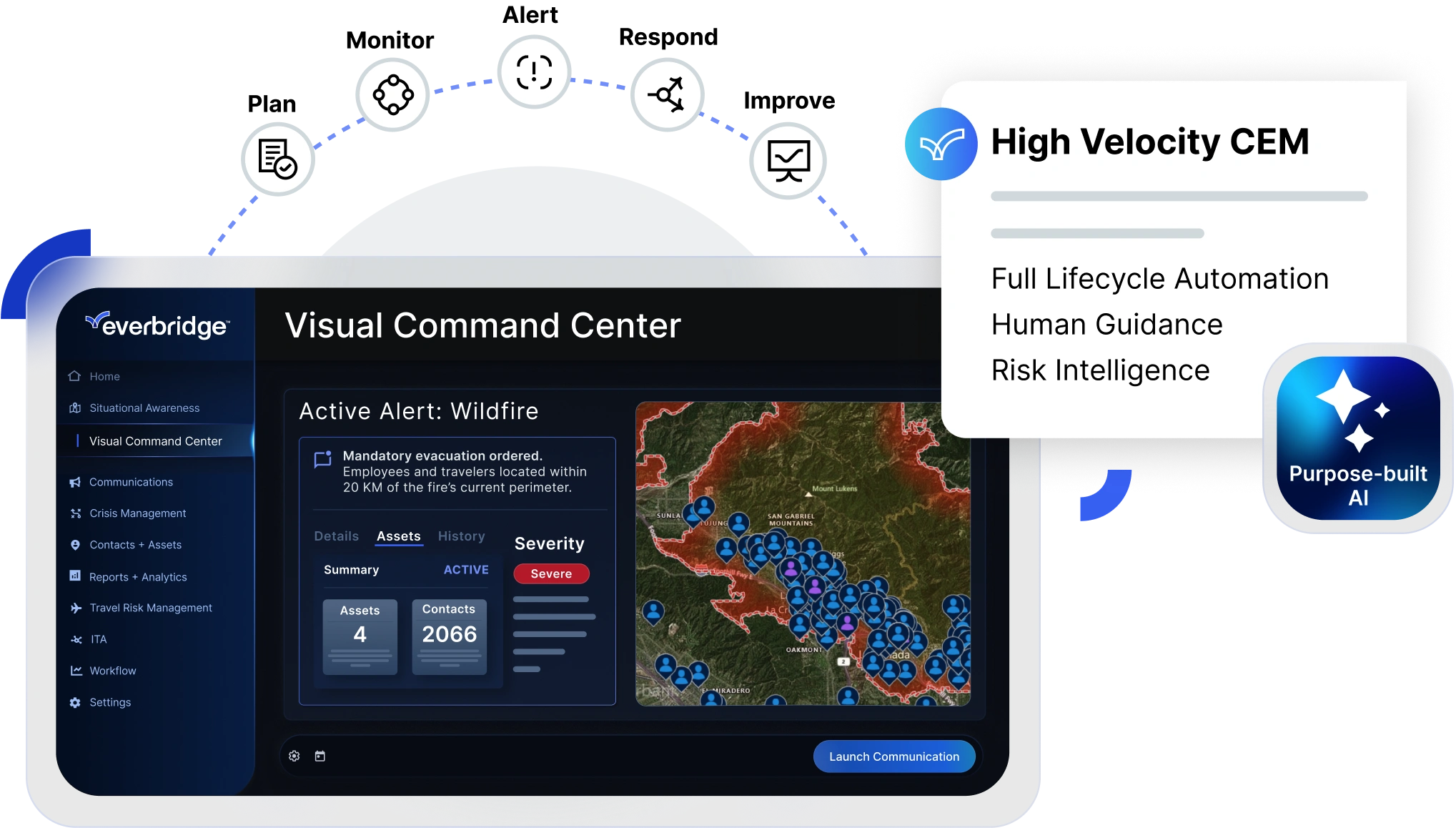
Everbridge Purpose-built AI
Transforming the way Everbridge customers manage operational risk, our Purpose-built AI empowers them to make faster, smarter decisions when it matters most.
Explore our Global Threat Outlook 2025, with critical strategies to navigate the complex risks ahead
Introducing a new era of CEM
Join CEO Dave Wagner as he unveils Everbridge High Velocity CEM, powered by Purpose-built AI. Discussing the strategic investment that paved the way, he highlights the company’s steadfast dedication to innovation, and the visionary leadership driving its success in the market.
Trusted by over 6,500 customers worldwide
By turning to Everbridge, high performing organizations are revolutionizing their approach to critical event management. With our innovative solutions, these organizations achieve response times 15x faster, safeguard revenue streams, and swiftly identify and alert employees about potential risks.

Everbridge named a Leader in The Forrester Wave™: Critical Event Management
Empower resilience with the leading critical event management platform.
According to Forrester, Everbridge CEM platform delivers 358% ROI
Forrester interviewed organizations with experience using the Critical Event Management platform who benefited from US$8.5M in three-year risk-adjusted benefits.
This includes:
- $3M in efficiency gains.
- $2M saved in reduced IT downtime.
- $1.5M in security team productivity gains.

See our customer reviews on G2